University expels student who called for accountability over Hong Kong fire
Discipline committee decides to terminate Miles Kwan from studies because of ‘multiple acts of misconduct’ A Hong Kong university student who had called for accountability over a deadly fire at an apartment complex in the city has been expelled by the school for disciplinary offences. Miles Kwan, a politics student, was detained for two nights by the city’s national security police last year for “seditious intent” after handing out flyers calling for an independent investigation into a fire that killed 168 people in November. Continue reading...

World's rules-based order 'no longer exists', Germany's Merz warns
"Our freedom is not guaranteed" in an era of big powers, the German chancellor tells Munich's security summit.
Europol signs Working Arrangement with the Argentine Republic
In December, the Ministry of National Security of the Argentine Republic and the European Union Agency for Law Enforcement Cooperation (Europol) signed a Working Arrangement in order to support the Member States of the European Union and Argentina in preventing and combating serious and organised crime and terrorism.The Working Arrangement provides for a structured legal framework for cooperation and enhanced...

Partial Federal Shutdown Shrinks Congressional Presence in Munich
In a moment of frayed trans-Atlantic relations, Speaker Mike Johnson abruptly canceled the House delegation to Europe’s biggest annual security summit.
Joint report outlines practical approach to prioritising post-quantum cryptography migration in financial services
A new joint report published by Europol and its partners provides financial institutions with a structured, risk-based approach to preparing for the transition to post-quantum cryptography. Advances in quantum computing are expected to challenge the long-term security of today’s encryption standards.

U.S. Transfers Thousands of ISIS Prisoners to Iraq From Syria
The moves appear to highlight lingering doubts in Washington about the new Syrian government’s ability to ensure security.

Congress Jets Off as D.H.S. Shuts Down
Despite a deadlock over funding for the agency, lawmakers left town and left Democratic and White House negotiators to try to work out a deal in their absence.

Congress Leaves DC as DHS Shuts Down
Despite a deadlock over funding for the agency, lawmakers left town and left Democratic and White House negotiators to try to work out a deal in their absence.
US and Europe must ‘repair and revive transatlantic ties’: Germany’s Merz
German leader seeks to set tone of unity at Munich Security Council, as top US diplomat says 'new era in geopolitics'.
Merz, Macron to address Munich Security Conference amid disputes with US
Ukrainian President Volodymyr Zelenskyy and US Secretary of State Marco Rubio will also address the conference.

Platforms bend over backward to help DHS censor ICE critics, advocates say
Pam Bondi and Kristi Noem sued for coercing platforms into censoring ICE posts.

A D.H.S. Shutdown Looms. Bruised Minnesotans Urge Their Parties to Dig In.
Congressional Democrats say they will approve no money for the Department of Homeland Security without guardrails on immigration agents. Their voters in Minnesota are demanding no less.
European leaders face tough talks at Munich Security Conference
European leaders return to the Munich Security Conference facing tough discussions on Ukraine, Greenland and NATO.
Prompt Injection Via Road Signs
Interesting research: “CHAI: Command Hijacking Against Embodied AI.” Abstract: Embodied Artificial Intelligence (AI) promises to handle edge cases in robotic vehicle systems where data is scarce by using common-sense reasoning grounded in perception and action to generalize beyond training distributions and adapt to novel real-world situations. These capabilities, however, also create new security risks. In this paper, we introduce CHAI (Command Hijacking against embodied AI), a new class of prompt-based attacks that exploit the multimodal language interpretation abilities of Large Visual-Language Models (LVLMs). CHAI embeds deceptive natural language instructions, such as misleading signs, in visual input, systematically searches the token space, builds a dictionary of prompts, and guides an attacker model to generate Visual Attack Prompts. We evaluate CHAI on four LVLM agents; drone emergency landing, autonomous driving, and aerial object tracking, and on a real robotic vehicle. Our experiments show that CHAI consistently outperforms state-of-the-art attacks. By exploiting the semantic and multimodal reasoning strengths of next-generation embodied AI systems, CHAI underscores the urgent need for defenses that extend beyond traditional adversarial robustness...
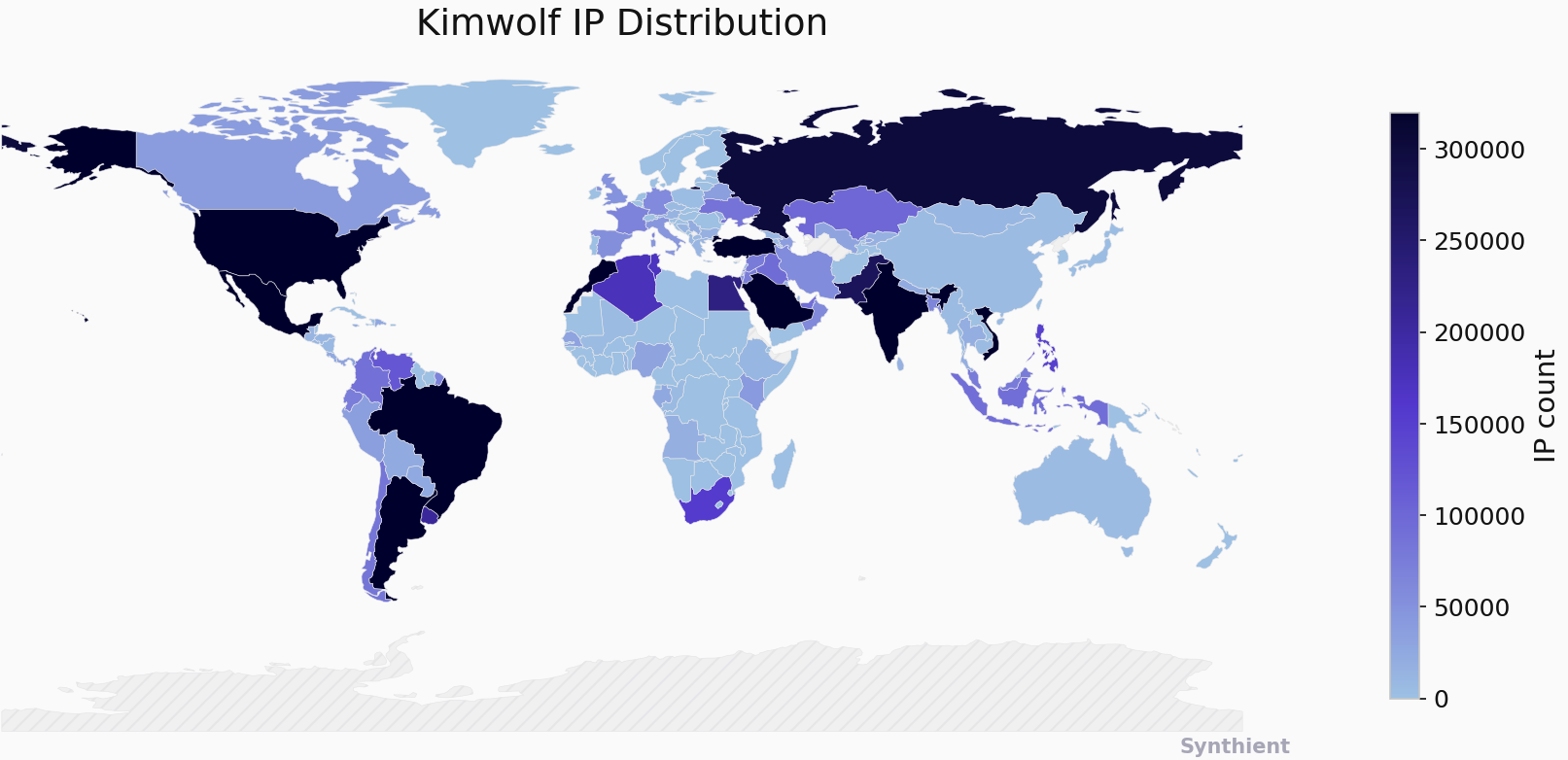
The Kimwolf Botnet is Stalking Your Local Network
The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it's time for a broader awareness of the threat. The short version is that everything you thought you knew about the security of the internal network behind your Internet router probably is now dangerously out of date.

Cisco erweitert AgenticOps mit KI für Netzwerk und Security
Systeme laufen jetzt im Agenten-Tempo, da können Betriebsmodelle auf menschlicher Geschwindigkeit nicht mithalten – so Cisco. Das soll künftig KI übernehmen.

Closing of El Paso Airspace Adds to Tension Between F.A.A. and Pentagon
The Federal Aviation Administration is charged with flight safety, and the Defense Department with national security. Those missions keep colliding.
Father of activist Anna Kwok convicted under Hong Kong national security law
Kwok Yin-sang arrested after he tried to end pro-democracy daughter’s insurance policy and withdraw funds A Hong Kong court has found the father of a wanted activist guilty of a national security violation, after he tried to end her insurance policy and withdraw the funds, drawing international criticism for the targeting of relatives of pro-democracy campaigners. Kwok Yin-sang, 68, is the first person to be charged under a homegrown national security law, also known as Article 23, for “attempting to deal with, directly or indirectly, any funds or other financial assets or economic resources” belonging to an absconder. Continue reading...
Hong Kong’s once-vibrant press stays silent or celebrates Jimmy Lai’s 20-year jail sentence
Lack of response shows security law and harassment by authorities have muzzled ‘critical voices’, say experts The rise and fall of Jimmy Lai, whose trajectory mirrored that of Hong Kong itself Hong Kong’s once-vibrant media outlets have responded with silence or celebration to the 20-year jail sentence handed down to Jimmy Lai, a pro-democracy media tycoon and critic of the Chinese Communist party. Lai, 78, was sentenced on Monday to 20 years in prison after being convicted of sedition and colluding with foreign forces under Hong Kong’s national security law. The charges were widely seen as being politically motivated and designed to silence one of Hong Kong’s most influential pro-democracy campaigners. Continue reading...
Dismantling Defenses: Trump 2.0 Cyber Year in Review
The Trump administration has pursued a staggering range of policy pivots this past year that threaten to weaken the nation’s ability and willingness to address a broad spectrum of technology challenges, from cybersecurity and privacy to countering disinformation, fraud and corruption. These shifts, along with the president’s efforts to restrict free speech and freedom of the press, have come at such a rapid clip that many readers probably aren’t even aware of them all.

Patch Tuesday, February 2026 Edition
Microsoft today released updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six "zero-day" vulnerabilities that attackers are already exploiting in the wild.

The DHS Shutdown Could Affect ICE, Travelers, FEMA and More
A lapse in funding probably won’t bring immigration enforcement operations to a screeching halt, but the department is also home to other agencies, including the Coast Guard and FEMA.

Patch Tuesday, January 2026 Edition
Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software. Eight of the vulnerabilities earned Microsoft's most-dire "critical" rating, and the company warns that attackers are already exploiting one of the bugs fixed today.

Leveraging OSINT for Corporate Security
To successfully protect people and assets, corporations must contend with several crime types, including theft of property, money, and data, intellectual property breaches, fraud, and cyber-attacks.

Here’s How a DHS Shutdown Could Affect ICE, Travelers, FEMA and More
A lapse in funding probably won’t bring immigration enforcement operations to a screeching halt, but the department is also home to other agencies, including the Coast Guard and FEMA.
‘Wake-up call’ for Greece as air force officer accused of spying for China
Christos Flessas detained in case seen as exposing Beijing’s strategy of infiltrating western military and security services A Greek air force officer arrested on suspicion of spying for China has been detained pending trial after appearing before a military judge in a case that is seen as exposing Beijing’s determination to infiltrate Europe’s security and intelligence services. Surrounded by armed escorts, a squadron leader identified as Col Christos Flessas emerged from the court late on Tuesday after giving testimony for more than eight hours. Continue reading...

Why Every Organization Needs an Intelligence-Driven Security Program
Crime, fraud, and insider threats can hit businesses from any angle, causing significant financial impact. Threats range from burglaries and shoplifting to fraud and harassment, amounting to less safe workplaces and hundreds of billions in losses for businesses each year.
heise+ | eBPF: Wie der Kernel programmierbar wurde
Der Artikel beschreibt, wie eBPF den Linux-Kernel programmierbar macht und dadurch neue Möglichkeiten in den Bereichen Networking, Security und Observability eröffnet.

DHS Shutdown Nears as Immigration Enforcement Talks Stall
Senate Democrats refused to move ahead with a spending bill needed to keep the Department of Homeland Security running because it lacked limits they have demanded on federal immigration agents.

Google recovers "deleted" Nest video in high-profile abduction case
In a notable abduction case, Google successfully recovered a deleted Nest video, highlighting the company's ability to retrieve video footage beyond the standard three-hour free storage limit provided to users.

What’s Coming to OSINT Live 2025
Each year, Skopenow’s OSINT Live gathers the leading minds in open-source intelligence to convey actionable tradecraft, proven workflows, and forward-looking strategies. Thousands of professionals from across government, corporate security, law enforcement, and more attend to learn how to sharpen their investigations and make smarter decisions.

Auditors at Bitpanda’s German subsidiary flagged information security issues, echoing regulator’s concerns
The crypto exchange said it had addressed authorities' concerns, but an internal report has cast doubt on those claims, according to a new investigation by ICIJ media partners.

Kyrgyz President Removes Close Ally From Top Security Post
The sudden removal of Kyrgyzstan’s powerful security chief ends a years-long political alliance that helped shape the country’s post-uprising leadership.
US border chief says ending ICE deportation surge in Minnesota
US border security chief Tom Homan says the Minnesota immigration crackdown is coming to an end.
LLMs are Getting a Lot Better and Faster at Finding and Exploiting Zero-Days
This is amazing: Opus 4.6 is notably better at finding high-severity vulnerabilities than previous models and a sign of how quickly things are moving. Security teams have been automating vulnerability discovery for years, investing heavily in fuzzing infrastructure and custom harnesses to find bugs at scale. But what stood out in early testing is how quickly Opus 4.6 found vulnerabilities out of the box without task-specific tooling, custom scaffolding, or specialized prompting. Even more interesting is how it found them. Fuzzers work by throwing massive amounts of random inputs at code to see what breaks. Opus 4.6 reads and reasons about code the way a human researcher would—looking at past fixes to find similar bugs that weren’t addressed, spotting patterns that tend to cause problems, or understanding a piece of logic well enough to know exactly what input would break it. When we pointed Opus 4.6 at some of the most well-tested codebases (projects that have had fuzzers running against them for years, ...

Happy 16th Birthday, KrebsOnSecurity.com!
KrebsOnSecurity.com celebrates its 16th anniversary today! A huge "thank you" to all of our readers -- newcomers, long-timers and drive-by critics alike. Your engagement this past year here has been tremendous and truly a salve on a handful of dark days. Happily, comeuppance was a strong theme running through our coverage in 2025, with a primary focus on entities that enabled complex and globally-dispersed cybercrime services.
.jpg)
Event Security: Using OSINT to Improve Safety and Operations
Event security has always relied on planning, coordination, and a visible presence. But in today’s environment, physical patrols and CCTV alone can’t keep up with the speed of information. Crowds move quickly, rumors spread even faster, and threats often appear online long before they surface at a venue.

The Role of OSINT in Executive Protection
Leaders are more visible and accessible than ever, which means their personal data, family details, and online presence all need the same level of protection as their physical movements. The most effective executive protection strategies blend digital intelligence with traditional security skills to quickly and proactively spot threats.

NY Democratic House Candidate Works for Palantir Partners Pushing AI Border Surveillance
A former Biden national security adviser hoping to unseat Mike Lawler consults for two defense tech firms that work with Palantir. The post NY Democratic House Candidate Works for Palantir Partners Pushing AI Border Surveillance appeared first on The Intercept.
Friday Squid Blogging: Squid Fishing Tips
This is a video of advice for squid fishing in Puget Sound. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Blog moderation policy.
Frequently Asked Questions
Q:What recent agreement did Europol sign?
Europol signed a Working Arrangement with the Argentine Republic.
Q:What does the joint report focus on regarding financial services?
The joint report outlines a practical approach to prioritising post-quantum cryptography migration in financial services.
Q:Who are the key speakers at the Munich Security Conference?
Merz and Macron are set to address the Munich Security Conference amid ongoing disputes with the US.
Q:What impact does the partial federal shutdown have on the Munich Security Conference?
The partial federal shutdown has resulted in a reduced Congressional presence at the Munich Security Conference.
Q:What challenges do European leaders face at the Munich Security Conference?
European leaders are expected to engage in tough talks at the Munich Security Conference.